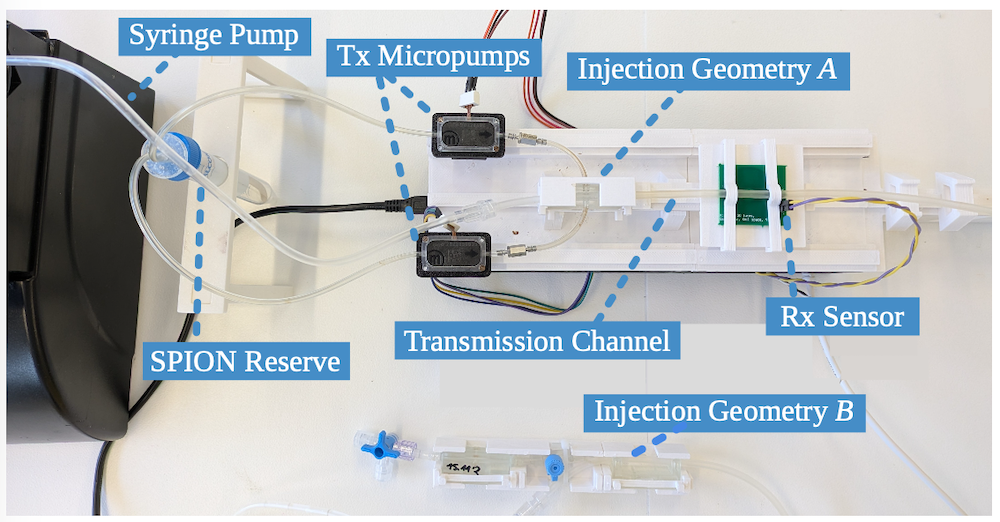
Personal website of
Felix Erlacher
Resources
This page contains additional resources to publications. This should make it easier to reproduce the presented results or reuse the presented tools. If there are any questions do not hesitate to contact the author.The FIXIDS system is available as a module (named IpfixIds) of the Vermont monitoring toolkit: https://github.com/felixe/ccsVermont under the branch http-aggregation.
Snort (v 2.9.11.1) is available at: https://snort.org/downloads/archive/snort/snort-2.9.11.1.tar.gz
Nprobe is available at: http://packages.ntop.org/
The TRex traffic generator is available at github
- Used snort.conf file: snort.conf
- Example Vermont IPFIX exporter configuration (as used in the evaluation part): vermontIpfixExporter.xml
- Example FIXIDS configuration (as used in the evaluation part): vermontFIXIDS.xml
- SIDs of all 5540 used Snort signatures (as used in the evaluation part): http.ruleSids. Because of license restrictions only the SIDs are given. The corresponding rules can be downloaded from the websites given in the paper.
- Attack traffic trace generated by GENESIDS (using the above 5540 signatures as input) as used for the functional evaluation in Section 5: attacks.pcap
SFR+500x6 trace:
This trace (used and described in the "Basic Throughput Experiments" section) was created by concatenating (and rewriting the IPs with tcprewrite) of this pcap trace, which was created by using TRex. Then we used Vermont with this configuration file to create the following binary file containing the aggregated IPFIX Flows: SFR+500x6.ipfix. The Flows of this file can be replayed by Vermont using the example IPFIX exporter configuration above and received and analyzed by FIXIDS using the sample FIXIDS configuration above.
To create the traffic used in Section 6.2 we used TRex and this configuration file. The attacks are created using GENESIDS. The name of the attack pcap trace includes the SID for the signature used as attack description. The following zip file contains 1000 attack traces, including the 100 used above:1000attacks.tar.gz. One pcap file contains the whole TCP stream used for the attack (as required by TRex).
- GENESIDS is available at: https://github.com/felixe/idsEventGenerator
- Input rules for GENESIDS/Snort supported.ruleSids
- Snort (v 2.9.11) is available at: https://snort.org/downloads/archive/snort/snort-2.9.11.tar.gz
- Used snort.conf file: snort.conf
- ATTACK TRACE: Sample attack trace generated with GENESIDS from the above rules and used as the first of 100 traces in the evaluation: genesidsAttackTrace.pcapng
Snort, with the above config and rule sids, detected 10728 alerts in this trace. 7883 true positives, 2845 false positives (711 unique false positives). 218 HTTP requests did not trigger the corresponding alert (false negatives).
- LABELS: List of port sid tuples, representing the port number of the TCP connection in the above trace containing an attack for the given sid (rule): genesidsAttackTrace.portSid
- SNORT ALARMS: List of port sid tuples, representing the alarms triggered by Snort when analyzing the above network trace: genesidsAttackTrace.snortPortSid
The FIXIDS system is available as a module (named IpfixIds) of the Vermont monitoring toolkit: https://github.com/felixe/ccsVermont under the branch http-aggregation.
Snort (v 2.9.9.0) is available at: https://snort.org/downloads/archive/snort/snort-2.9.9.0.tar.gz
Nprobe is available at: http://packages.ntop.org/
The following configuration files were used in the evaluation part:
- Snort configuration files: fixidsSnortConfs.tar.gz
- Snort rules list: fixidsRulesList.tar.gz
- Vermont configuration files for FIXIDS receiving Flows: fixids.xml
- Vermont configuration files for the "monolithic" FIXIDS configuration: monolithicFixids.xml
- Command to make nprobe export http IE nprobe.sh
These are the additional 20 attacks (as pcap network traces) that we generated and inserted into the test network trace. The name represents the sid of the snort rule triggering the corresponding event: fixidsAttacks.tar.gz
For privacy reasons the proxy network trace can not be published.
The Vermont monitoring toolkit iis available at: https://github.com/felixe/ccsVermont under the branch http-aggregation.
Snort (v 2.9.9.0) is available at: https://snort.org/downloads/snort/snort-2.9.9.0.tar.gz
The following files were used in the evaluation part:
- Snort configuration files: snortConfs.tar.gz
- Snort rules list: httpRulesUniqueList.tar.gz
- Vermont configuration files: vermontConfs.tar.gz
These are the attacks that we generated and inserted into the test network trace. The name represents the sid of the snort rule triggering the corresponding event: sid2010051.pcapng
sid2010054.pcapng
sid40357.pcapng
sid27244.pcapng
sid39190.pcapng
For privacy reasons the other network traces can not be published.
https://bitbucket.org/swoertz/master-project
https://github.com/felixe/ccsVermont under the branch http-aggregation.
Below are network dumps in the libpcap format used in the evaluation part of the above paper:
The first two dumps used in Table I are taken from the "Wireshark Network Analyst Study Guide" by L. Chapelle and can be downloaded from http://www.wiresharkbook.com/studyguide.html, search for "Book Supplements".
The pipelining dump was created using opera and connecting, among others, to a Dropbox account. For privacy reasons this dump is not published.
The anomalous dump can be downloaded from the wireshark wiki
Dumps used in Table II:
Trace 1: Trace created by capturing the network traffic of a scientific work group for a week. This trace can not be published because it contains confidential information.
Trace 2: Trace created by using the web crawling framework crawl-mtu1000-run1.anon.pcap.gz
Trace 3: Same as trace 2, different properties, anonymized: crawl-mtu1000-run2-part2.anon.pcap.gz
Trace 4: Same as trace 2, different MTU, different properties, anonymized: crawl-mtu1500-run1-part4.anon.pcap.gz
Other dumps used for the evaluation, but not shown in the paper for space reasons, are taken from http://digitalcorpora.org/corpora/scenarios/m57-patents-scenario.

The network dumps are licensed under a Creative Commons Attribution-NonCommercial-ShareAlike 4.0 International License.
Please read and follow the copyright restrictions on the above linked sites.